

| Live Chat by AliveChat |

International Walkie Talkie - VoIP SoftSwitch Technology

The next generation broadband networks are interconnected and include elements from traditional PSTN, mobile and IP Telephony in addition to pure data. A mechanical transfer of the Class IV voice switch functionality onto IP Telephony Softswitches is sub-optimal. Softswitch takes full advantage of the features specific to IP Telephony protocols.
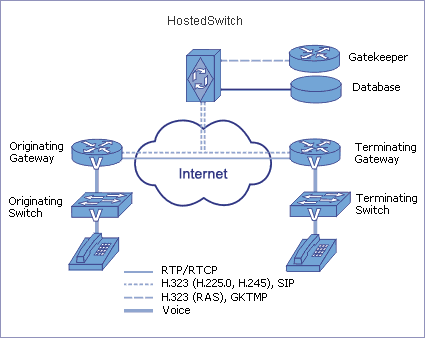
HostedSwitch enables carriers to provision in the most secure manner thousands of VoIP gateways / gatekeepers independent of their manufacturer (including Cisco / Vocaltec / Clarent / Quintum). Additionally, the session controlling functionality of HostedSwitch enables connected companies to obtain Call Detail Records and other data in real time.
A typical IP Telephony call consists of two logical parts: call control and voice streams. H.323 or SIP protocols govern call control while RTP/RTCP carries the voice. HostedSwitch transmits only H.323 and SIP call signaling. The originating and terminating gateways establish a direct voice path bypassing SoftSwitch that opens (closes) the session once one of the gateways declares the beginning (end) of the call.
HostedSwitch reaches additional flexibility in managing voice streams because it modifies Protocol Signaling Units sent between the gateways. That allows companies connected to HostedSwitch to interoperate gateways otherwise not operable because of inconsistent implementation of H.323 and/or SIP by different manufacturers.
Security
Carriers using IP Telephony face more stringent security requirements than enterprises or calling card operators due to a much larger number of gateways/gatekeepers they have to manage. The HostedSwitch platform provides an elegant solution that greatly facilitates the process of secure provisioning.
SoftSwitch Instance receives a static IP address. The terminating gateway receives the control signaling (TCP) only from that address, unique to each carrier. Thus, the key security requirement for any Firewall Policy is to deny TCP (ports 1720 and 5060) to/from all external hosts except Softswitch.
The Recommended Firewall Policy is to Permit UDP (ports higher than 1024, except 5060) to/from ANY IP addresses. Then the voice traffic (UDP) can come from the call-initiating gateway with virtually any IP address, as long as HostedSwitch authorizes that particular call. This way you will ensure that all traffic authorized by HostedSwitch will land at your gateway.
A Dated Firewall Policy is to permit UDP (ports higher than 1024, except 5060) ONLY to/from SPECIFIC IP addresses. This policy has a significant overhead in terms of time, costs, and security risks as the result of human errors appearing in the process of maintaining the list of trusted gateways.
Both policies have the same class of the security when it comes to VoIP calls. It may seem insecure to allow the UDP traffic from the Internet to penetrate the firewall, but in the case of H.323 calls, voice traffic over UDP will not start until the control part of a call is completed over TCP. Therefore, it is sufficient to block the TCP stream in order to prevent unauthorized traffic from being sent to/from your gateways.
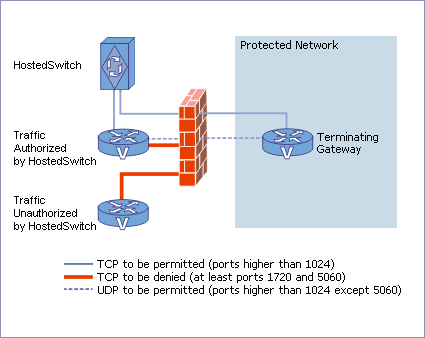
Figure 2. Using a firewall to block unauthorized traffic
Interoperable VoIP equipment
- H.323-compliant gateways and gatekeepers
- SIP-compliant gateways and proxies
- Agat-RT AVG VoIP equipment
- Antek Networks Inc. VoIP equipment
- AudioCodes VoIP equipment
- Avaya (Lucent Technologies) VoIP equipment
- Cisco ATA186, 1750, 18xx, 26xx, 28xx, 36xx, 38xx, AS53xx, AS54xx, 7200 other Cisco equipment with VoIP modules and IOS versions later 12.1.
- Clarent VoIP equipment
- Computer Protocol (Malaysia)
- Dialogic IPLink VoIP equipment
- Dialpad soft phone
- D-Link VoIP equipment
- ECI Telecom I-Gate 1000
- Equivalence (Open H.323)
- EyeP Media VoIP equipment
- Incomtel TG (Russia) Softswitch
- Intel VoIP equipment
- MediaRing Proxy Server
- MiBridge VoIP equipment
- MERA VoIP Transit Softswitch
- Asterisk soft PBX
- GNU Gatekeeper
- MockingBird Networks GW
- MultiTech VoIP equipment
- OKI Network Technologies GW
- Opto Telelinks (Germany)
- ProxySER SIP proxy server
- Quintum GW Tenor series.
- SoftJoys Labs VoIP equipment
- Sonus Networks VoIP equipment
- Sipura VoIP adapters
- Telogy Networks (TI's company)
- Vive GSX9000
- VocalTec VGW 4/8/120/480/2000, IPL 6.x, Surf&Call
- VEA versions: 1.3, 1.4, 1.5, 2.0
- VGW120 versions: 4.3, 4.4, 4.5, 20.1
Vocord Telecom GW
Supported Call Control Protocols
- ITU H.323, Versions 2, 3, 4, 5
- FastStart and SlowStart scenarios
- Interdomain GK support through LRQ messages
SIP, Version 2
- GKTMP (Cisco Gatekeeper Transaction Message Protocol) V. 1.0 - 3.01
- LRQ, ARQ, and RRQ messages
Interoperability between H.323 and SIP Protocols in both directions
The HostedSwitch Management
Management of thousands of GW-GW, GK-GW, and GK-GK from a single location
- Integration of networks independent of Gatekeeper or Proxy Registrar
- Web-based access and interface
- Additional security due to network isolation
- Multiple translation rules and intelligent routing algorithms
- Billing System provides Call Detail Records in real time



























